Poste Italiane phishing emails 2
In this hours a "new" phishing attack is targetting Poste Italiane and his service called Postepay. In the previous article regarding poste italiane phishing email the phiser to convince the victim to send their account details said that they won a bonus of 250 euro.
This time he chose another way that is more credible (in my opinion).
The title says we detected irregular activity on your Poste Italiane account and the content proceed for your protection you must download the attachment and fill the form. If you ignore this email your account will be temporarily suspended.
The sender is support@update.com
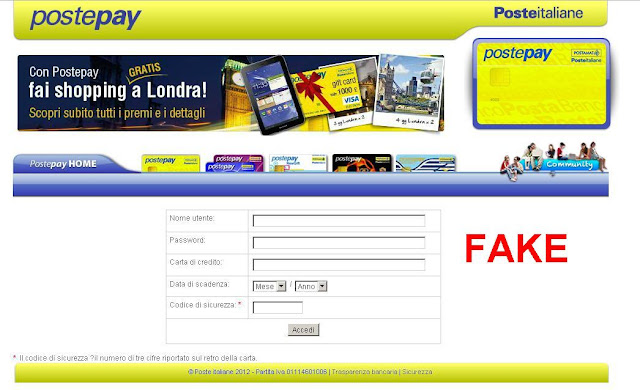
When you open the attachment you get this page with a central form ready to be filled with postepay account details (Username, Password, Credit Card Number, Expiration Date, Security Code).
In this file he haven't tried to obfuscated the form code as he did last time, so the address of the server where the data will be sent is easily visible.
This server is located in Poland and the ISP is Netia S.A.
There aren't domains that point to this ip address.
The server is running a copy of Windows Server 2003 with Apache2Triad which is a sort of WAMP only that the project is a dead since 2009. If you browse to this address the index page will look like this.
He created an index that doesn't list the other files on the server. As you can image sobo.php script collect the stolen data, save this information in a txt file or send an email to the phisher and at the end redirect the victim to the original site. What will be its content ?
Downloaded with wget, so no php: index page
I was expecting to see a meta tag or nothing, instead i found a copy of Poste Italiane website. Here it is a screenshot posted on PhishTank.
Maybe this mean that he started redirecting the victims to this site and then stole the information, now he sends an attachment.
That's all for now.
This time he chose another way that is more credible (in my opinion).
The title says we detected irregular activity on your Poste Italiane account and the content proceed for your protection you must download the attachment and fill the form. If you ignore this email your account will be temporarily suspended.
The sender is support@update.com
When you open the attachment you get this page with a central form ready to be filled with postepay account details (Username, Password, Credit Card Number, Expiration Date, Security Code).
This server is located in Poland and the ISP is Netia S.A.
There aren't domains that point to this ip address.
The server is running a copy of Windows Server 2003 with Apache2Triad which is a sort of WAMP only that the project is a dead since 2009. If you browse to this address the index page will look like this.
He created an index that doesn't list the other files on the server. As you can image sobo.php script collect the stolen data, save this information in a txt file or send an email to the phisher and at the end redirect the victim to the original site. What will be its content ?
Downloaded with wget, so no php: index page
I was expecting to see a meta tag or nothing, instead i found a copy of Poste Italiane website. Here it is a screenshot posted on PhishTank.
Maybe this mean that he started redirecting the victims to this site and then stole the information, now he sends an attachment.
That's all for now.





Comments
Post a Comment